Setting up a screening rule
Rule creation
Create a screening rule is to be done from a scenario, in the rules section.
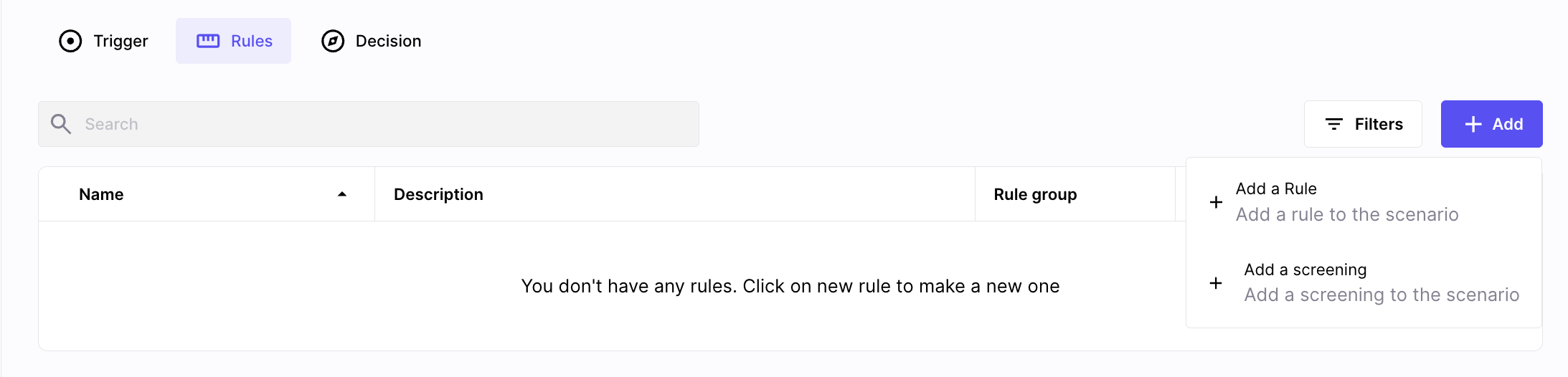
create a new screening rule
Rule configuration
Global organization configuration of screenings
- Similarity matching threshold: it is the minimum similarity score (as a %) for an entity to be considered a possible match on a sanction list.
The default value is 70%, which we believe is a reasonable base value in most cases : higher values will result in less hits, at the risk of missing some true positives.
In this section you can override the default similarity threshold, this newly defined threshold will be used only for this rule.
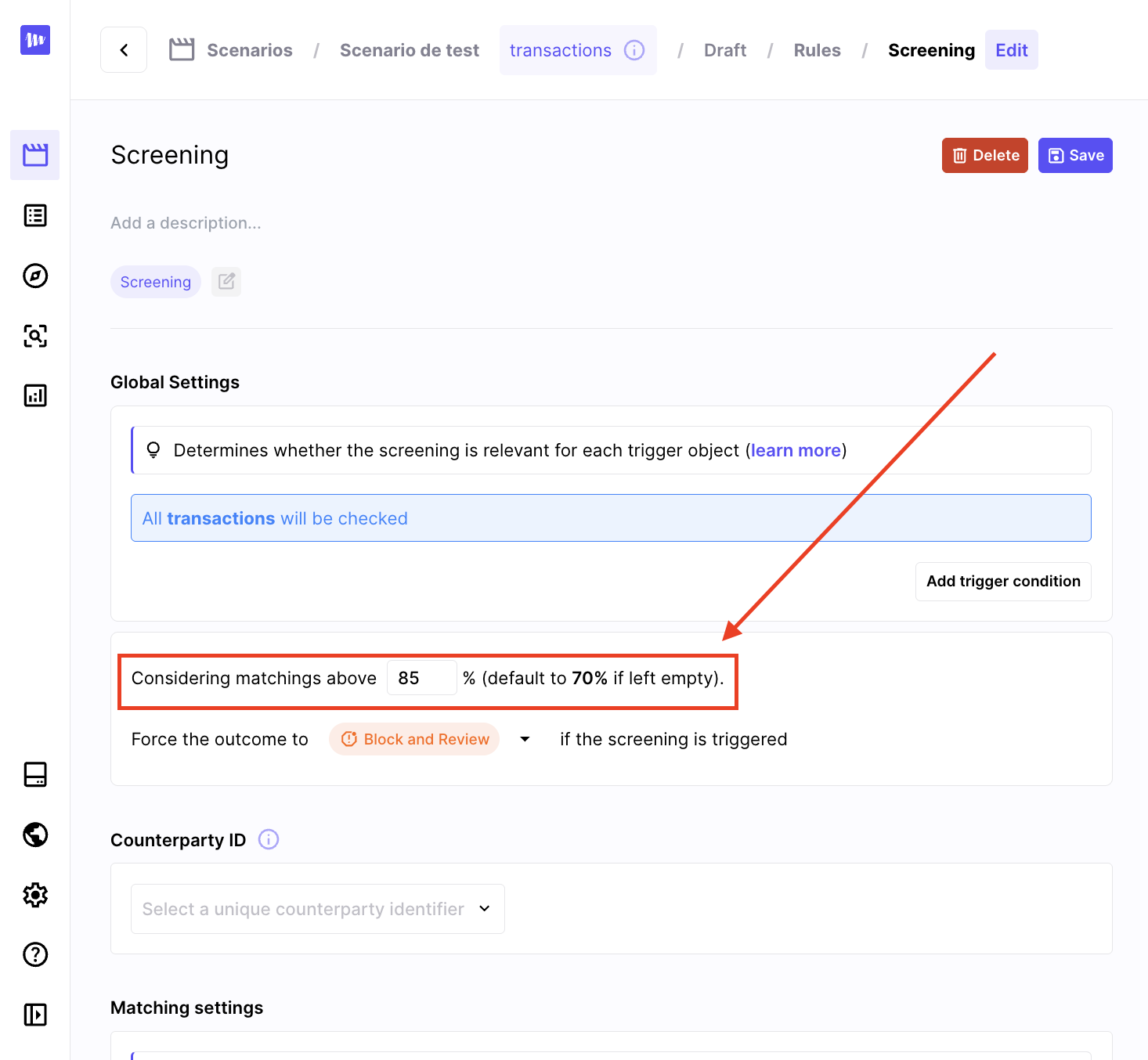
In this example, the similarity threshold will be 85% despite the default value being 70%
- A max number of hits to consider is also defined at the organisation level : it is the maximum number of hits for a screening review with store. If a screening has more hits than this, the reviewer will be asked to refine the search before he can close the case. See the refine page. The default value is 30.
The organization sanction check settings are configured by an administrator in Marble Settings > Scenarios.
Specific rule configuration
The body of a screening rule is configured a bit differently from a regular scenario rule. It expects the following settings:
| configuration | format | effect |
|---|---|---|
| trigger condition | A trigger condition formula, in the same format as the trigger condition defined at the scenario level. | Used to only perform thescreening on payloads triggering the scenario that pass certain conditions. |
| forced outcome | A similarity threshold (default value if null) and an outcome among: review, block_and_review, decline | If the screening has at least one possible match (above defined threshold), it forces the outcome of the decision. This overrides any outcome determined from the aggregated score of the other rules. |
| counterparty ID | Select a field from the payload that will be used for whitelisting. | In case of false positive, you can whitelist future matches based on the counterparty identifier you selected. Typically, the value would be an account number, IBAN or crypto wallet hash. |
| matching settings | Select and transform fields from the payload or ingested data to be used for the sanctioned entity search. | See details below. |
| set of lists to filter on | Consolidated lists from Opensanctions, grouped by geographic region for convenience. | Selects the sanction, PEP, adverse media or thirs parties lists that are taken into account for screening in the scenario. |
Details on matching settings
There are several settings that can be configured in your screening:
- entity type: chose among Person, Organization or Vehicle to limit false positives, or just select Any type to screen against all types
- name: select one or more fields that form the full name of the entity you are screening. It could be the addition of first_name and last_name or only full_name for example
- screening options: you have four options available to fine tune your screening:
- Exclude terms listed in custom lists: remove any terms (like recurring terms such as Mr, Mrs for example), defined in one of your lists. You need to create a custom list first, in the Lists section
- Exclude numbers: remove all numbers from the entity name to only keep alphabetical characters
- Do not screen very short words: define a minimum number of characters, below which the screening will be skipped to avoid noise
- Enable AI name recognition: Use AI to extract person or company names from free-form text and use it for a more precise screening.
Note this is an experimental feature and may significantly increase the response time when requesting decisions.
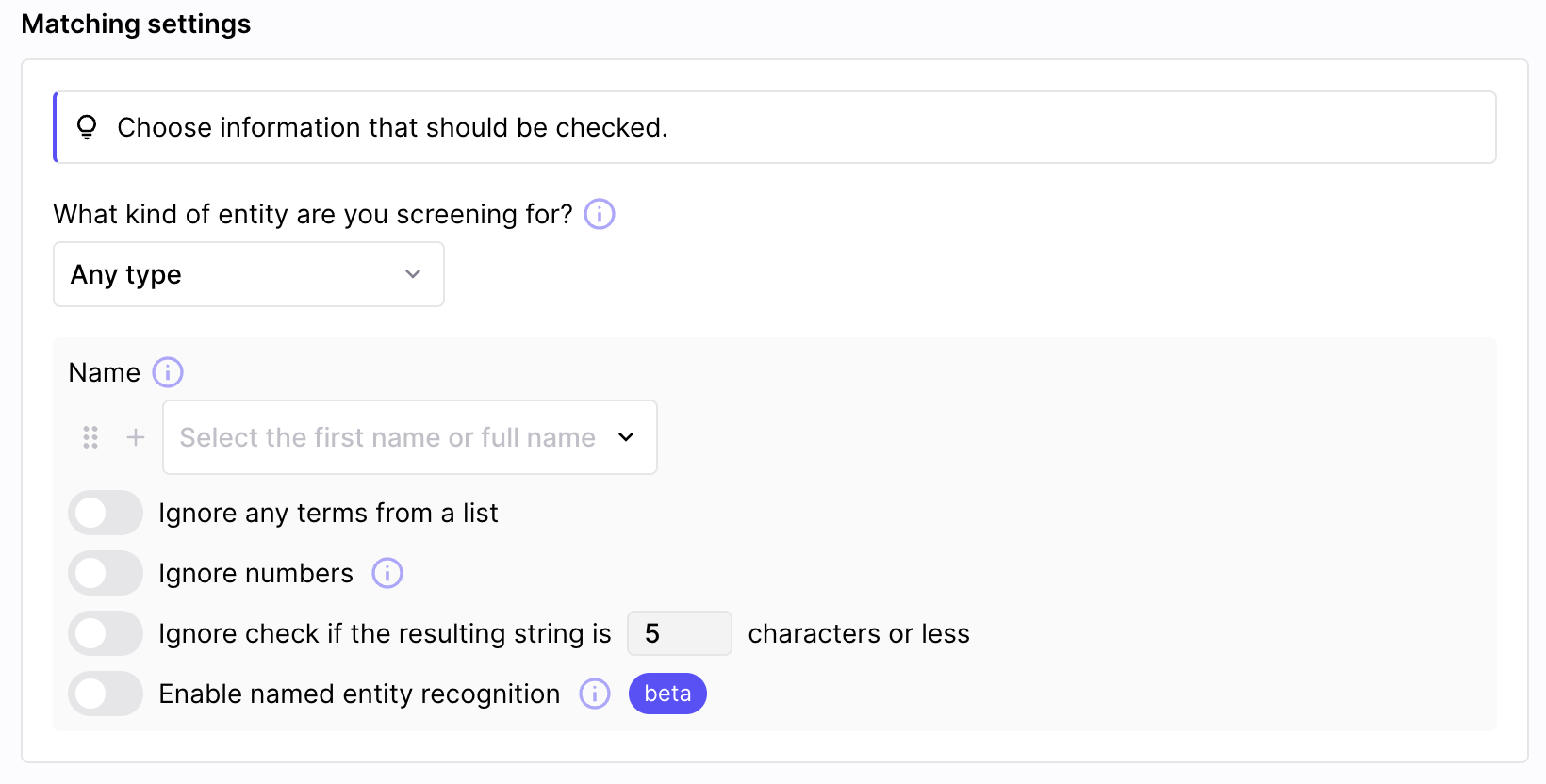
Matching options help you narrow your screenings and reduce noise
Updated 4 months ago